How to Setup GitHub OAuth for JupyterHub¶
This guide will walk you through the process of setting up GitHub OAuth for your JupyterHub deployment.
Prerequisites¶
A GitHub account
Administrative access to your JupyterHub deployment
Your JupyterHub domain/URL
Step 1: Create a New GitHub Organization¶
Go to github.com and click on
+icon in the top rightClick New Organization from the dropdown menu
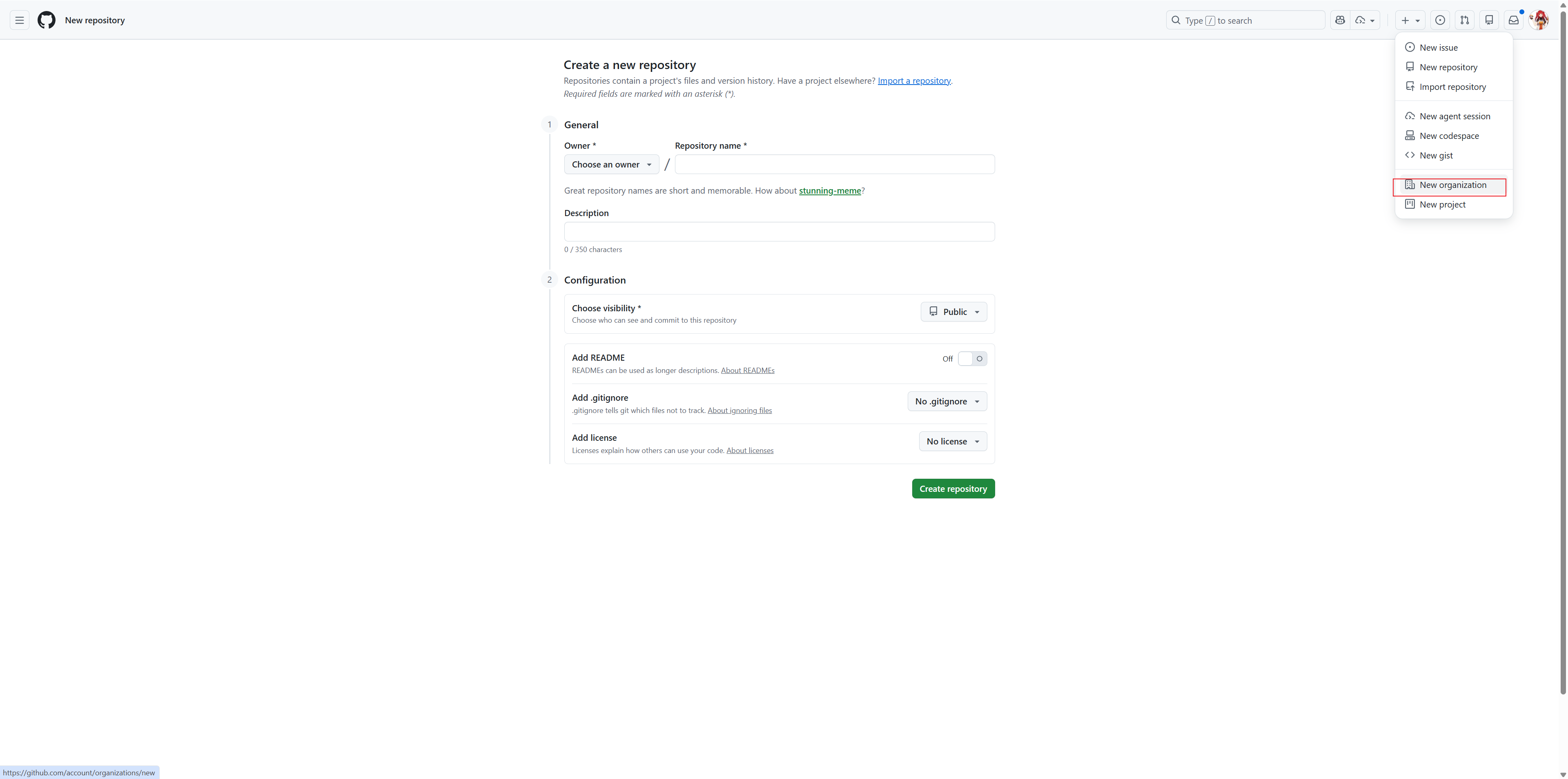
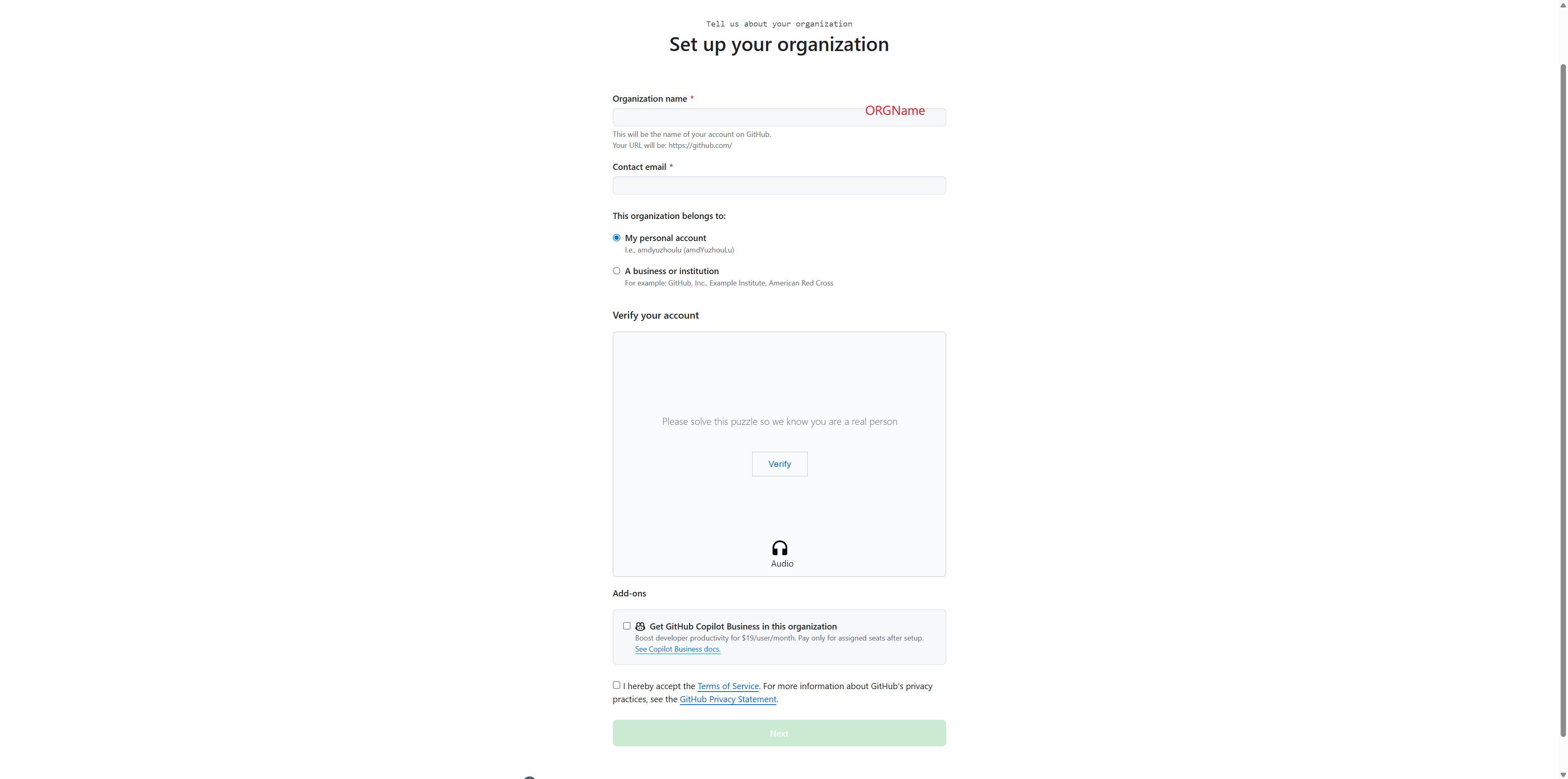
Fill in the organization details:
Enter your Organization name (e.g., “AUP-INT-TEST”)
Provide a Contact email
Select whether this organization belongs to “My personal account” or “A business or institution”
Complete the verification puzzle
Accept the Terms of Service
Click Next to create the organization
Step 2: Create Teams to Assign Different Permissions¶
Teams allow you to organize members and control access to different resources in your JupyterHub deployment.
Navigate to your organization’s Teams page
Click the New team button in the top right
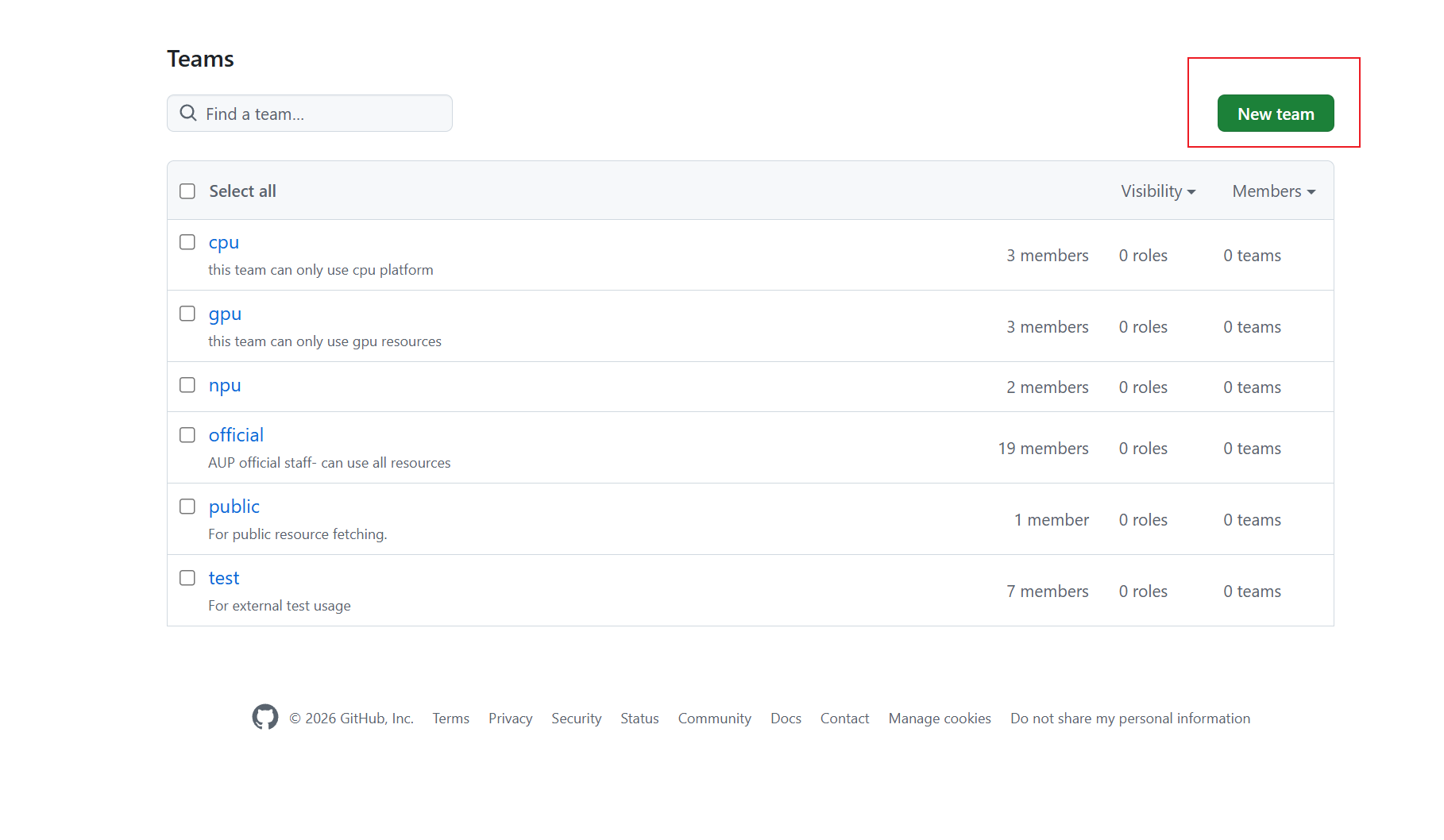
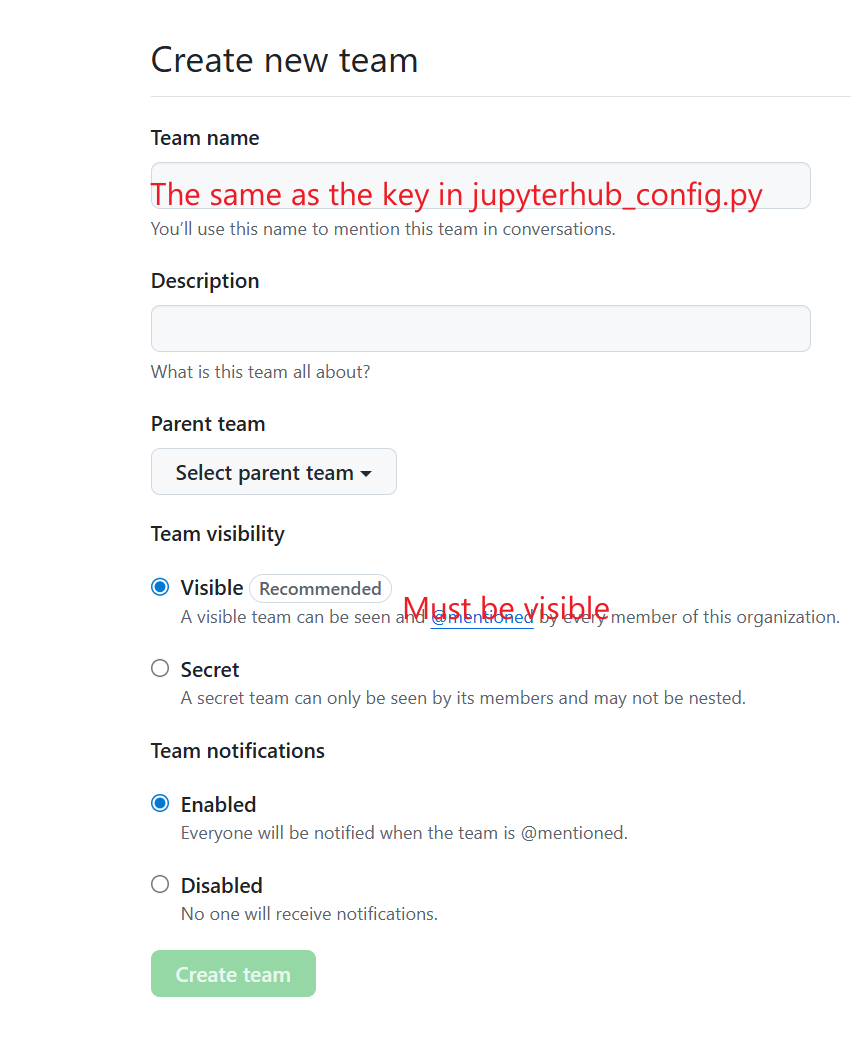
Fill in the team creation form:
Team name: Use the same name as the key in your
jupyterhub_config.py(e.g., “cpu”, “gpu”, “npu”, “official”)Description: Add a description of what this team is for
Team visibility: Select Visible (recommended) - this allows all organization members to see the team
Team notifications: Choose whether to enable notifications
Click Create team
Repeat this process to create all the teams you need for your resource mapping (e.g., cpu, gpu, npu, official, public, test)
Step 3: Add Members to the Organization¶
Go to the People tab in your organization
Click the Invite member button in the top right
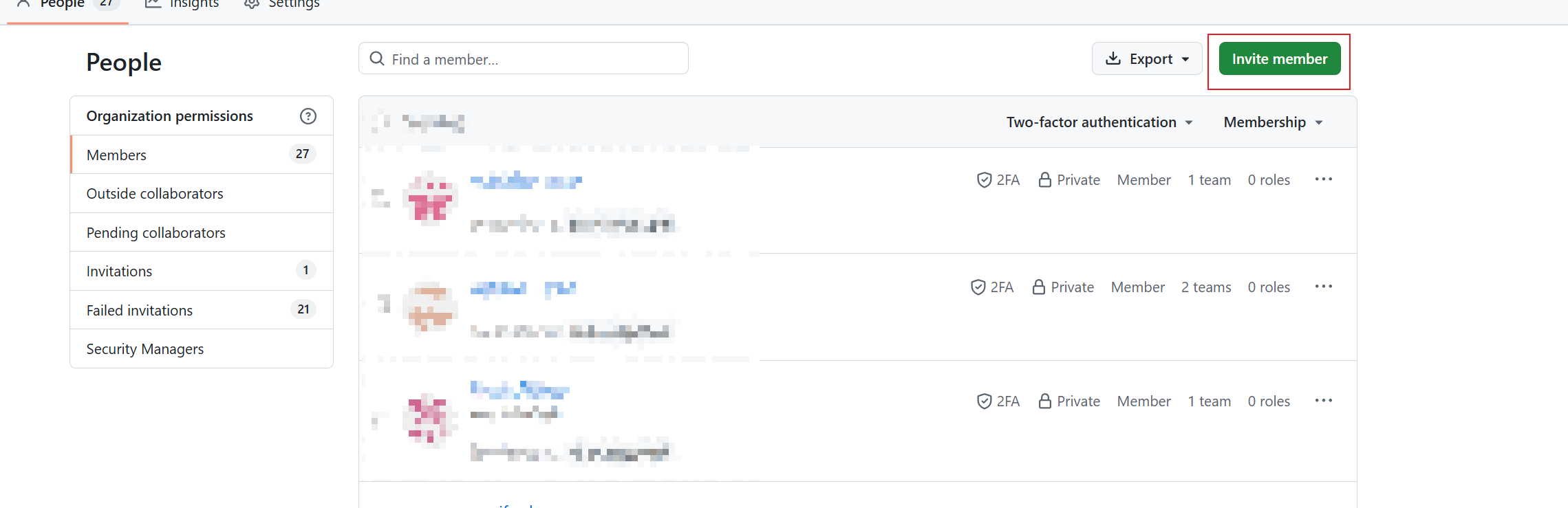
In the invitation dialog:
Enter the member’s email address or GitHub username
Click Invite
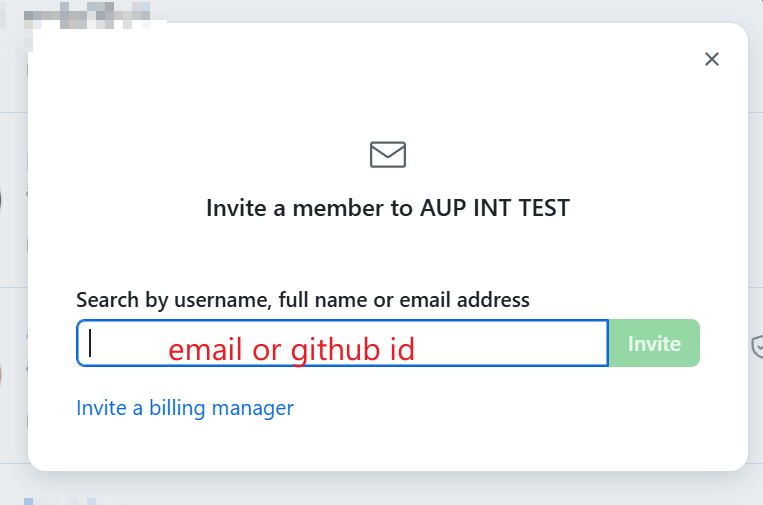
Assign the member to appropriate teams and roles:
Role in the organization:
Select Member for normal users (can see all members and be granted access to repositories)
Select Owner for admin users (full administrative rights to the organization)
Teams: Select the teams this member should belong to (e.g., cpu, gpu, official)
Click Send invitation
Repeat this process for all members you want to add to your organization
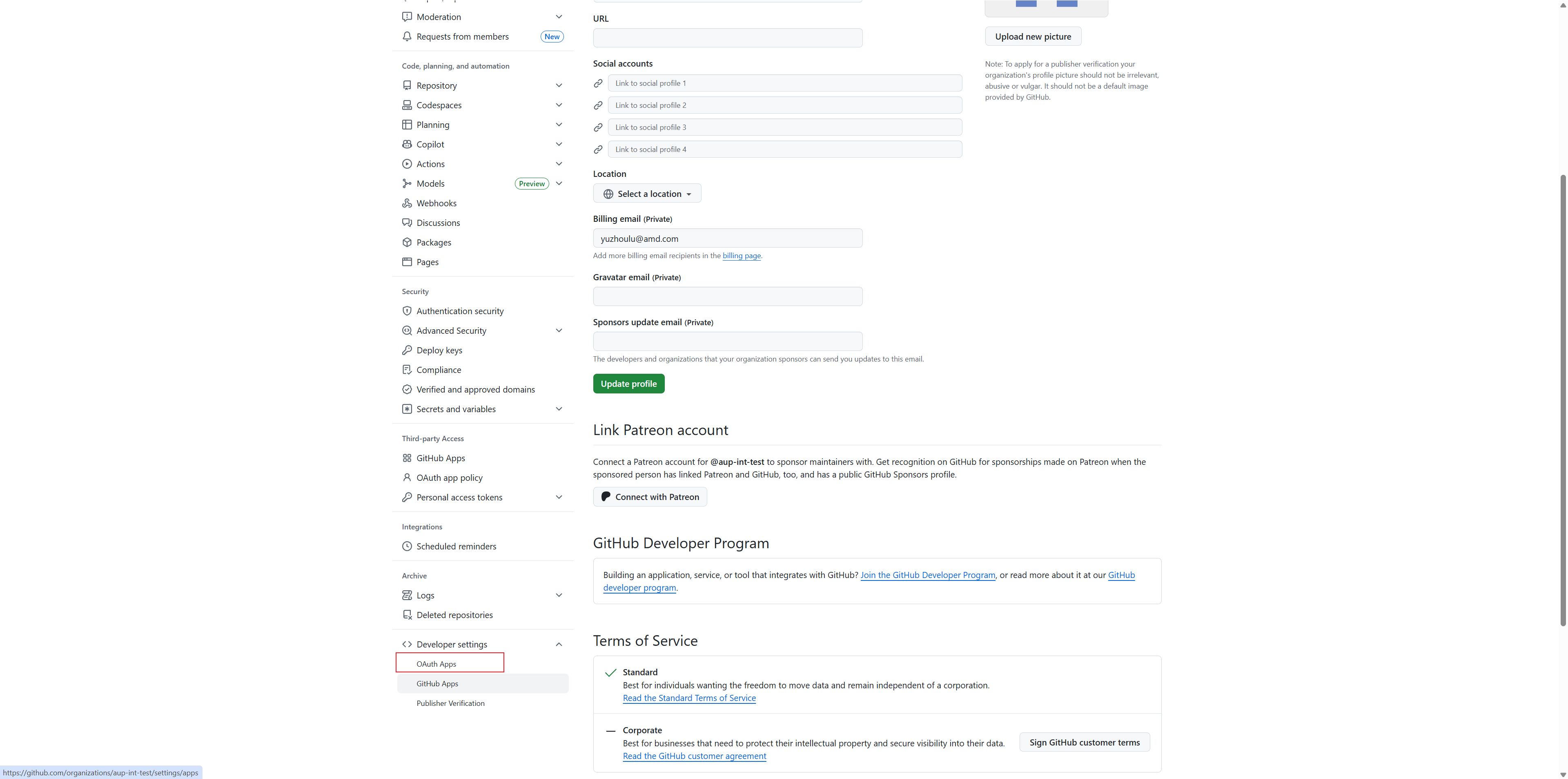
Step 4: Create a GitHub OAuth App¶
Go to your organization settings:
github.com/<your-organization>/settingsIn the left sidebar, scroll down to Developer settings
Click OAuth Apps
Click New OAuth App
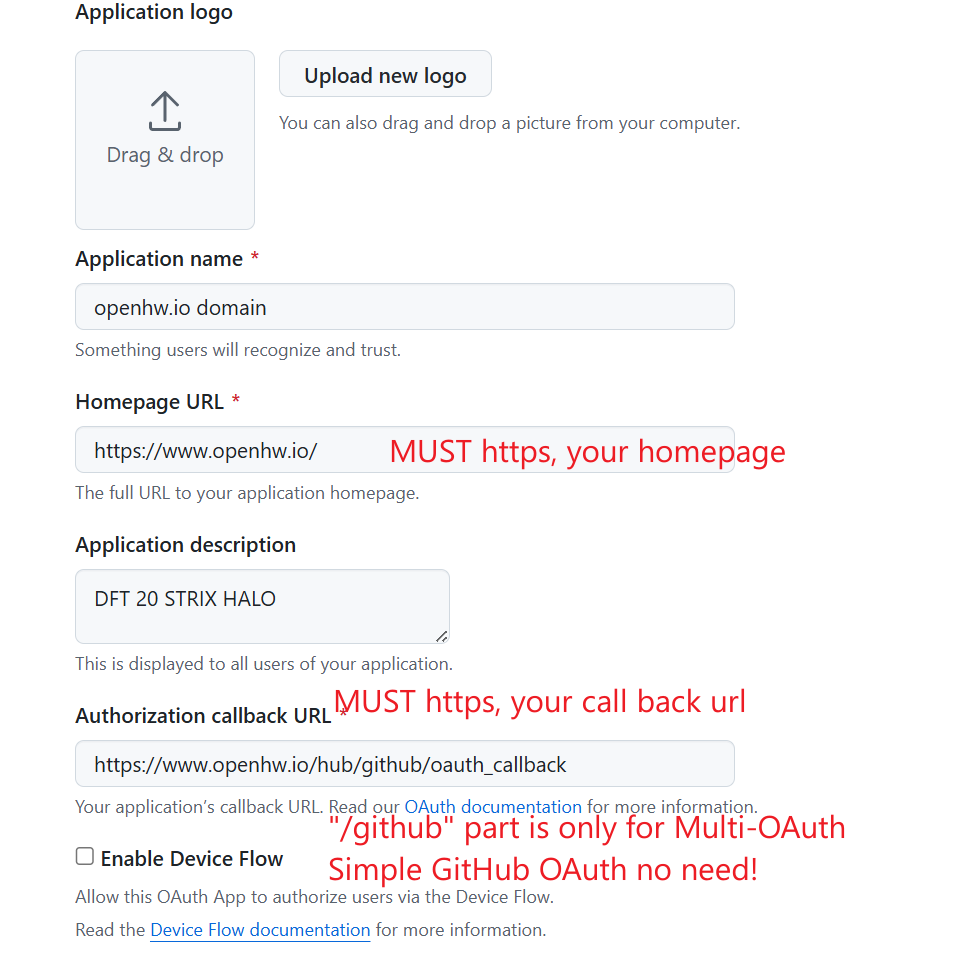
Fill in the OAuth application registration form:
Application name: Your domain name (e.g., “openhw.io domain”)
Homepage URL: Your JupyterHub homepage URL (e.g.,
https://www.openhw.io/)Important: Must use HTTPS protocol
Application description: Brief description of your application (optional)
Authorization callback URL: Your OAuth callback URL
Format:
https://<your-domain>/hub/oauth_callbackExample:
https://www.openhw.io/hub/oauth_callbackImportant: Must use HTTPS protocol
Note: The “/github” part in the URL is only needed for Multi-OAuth setups. For simple GitHub OAuth, use the format shown above.
Enable Device Flow: Leave unchecked (not needed for JupyterHub)
Click Register application
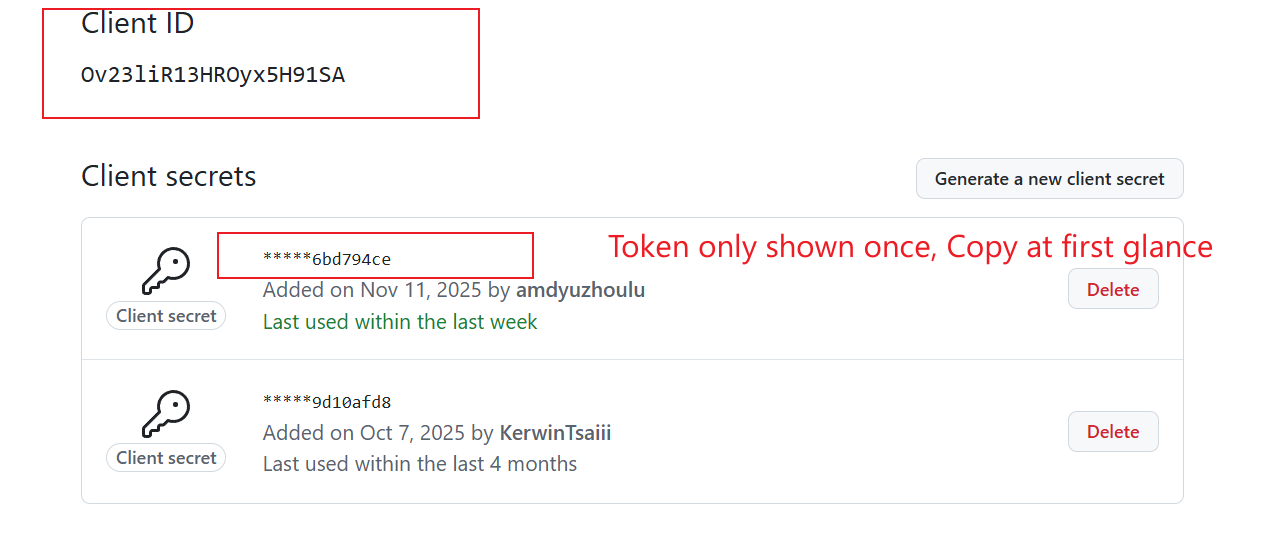
After registration, you will see your Client ID and Client secrets:
Copy the Client ID - you’ll need this for your JupyterHub configuration
Click Generate a new client secret
Important: Copy the client secret immediately - it will only be shown once!
Store both the Client ID and Client secret securely
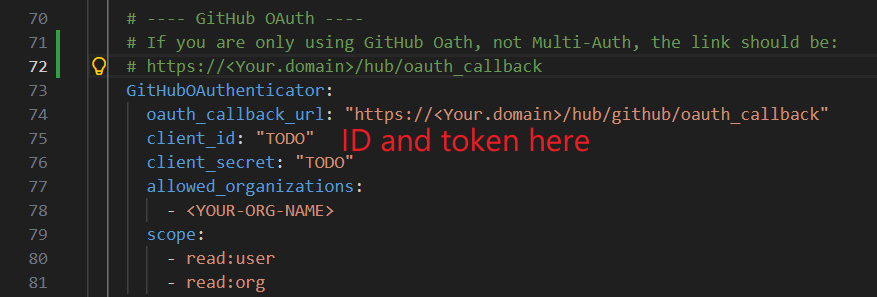
Step 5: Configure JupyterHub for GitHub OAuth¶
Open your JupyterHub configuration file (typically
jupyterhub_config.pyorvalues.yamlfor Helm deployments)Add the GitHub OAuth configuration:
# ---- GitHub OAuth ---- # If you are only using GitHub OAuth, not Multi-Auth, the link should be: # https://<Your.domain>/hub/oauth_callback GitHubOAuthenticator: oauth_callback_url: "https://<Your.domain>/hub/oauth_callback" client_id: "YOUR_CLIENT_ID" client_secret: "YOUR_CLIENT_SECRET" allowed_organizations: - <YOUR-ORG-NAME> scope: - read:user - read:org
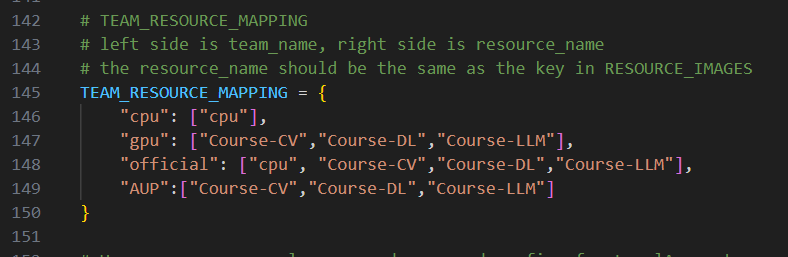
Configure team-to-resource mapping on
jupyterhub_config.py:# TEAM RESOURCE MAPPING # left side is team_name, right side is resource_name # the resource_name should be the same as the key in RESOURCE_IMAGES TEAM_RESOURCE_MAPPING = { "cpu": ["cpu"], "gpu": ["Course-CV", "Course-DL", "Course-LLM"], "official": ["cpu", "Course-CV", "Course-DL", "Course-LLM"], "AUP-IT": ["Course-CV", "Course-DL", "Course-LLM"] }
Update the organization in
jupyterhub_config.pyfile
Search for the following line and update the name of your GitHub organization
team["organization"]["login"] ==
Save the configuration file and restart JupyterHub for the changes to take effect
Verification¶
Navigate to your JupyterHub URL
You should see a “Sign in with GitHub” button
Click it and authorize the application
You should be redirected back to JupyterHub and logged in
Verify that users can only access resources based on their team membership
Troubleshooting¶
OAuth callback error: Ensure your callback URL exactly matches what you configured in GitHub (including HTTPS)
Organization not found: Verify the organization name in your configuration matches your GitHub organization exactly
Users can’t access resources: Check that users are added to the correct teams in GitHub
Authentication fails: Verify your Client ID and Client Secret are correct and the secret hasn’t expired
Security Best Practices¶
Always use HTTPS for your JupyterHub deployment
Keep your Client Secret secure and never commit it to version control
Regularly review organization members and their team assignments
Use environment variables or secret management systems for storing OAuth credentials
Limit OAuth scopes to only what’s necessary (read:user and read:org)